Over the last twenty-five years there has been a significant increase in the complexity and ingenuity of attacks aimed at operational technology (OT) environments. The complexity has also led to increased unintentional impacts. This upsurge is not just a matter of scale but of the nature of the threats themselves, which have become increasingly tailored to exploit the specific vulnerabilities of enterprise information technology (IT) systems, the growing interdependency between IT and OT, and the increased connectivity of process control and automation environments. These process control and automation environments have become prime targets for cybercriminals, nation-states, and hacktivists due to their pivotal role in national security, public safety, and the economy.
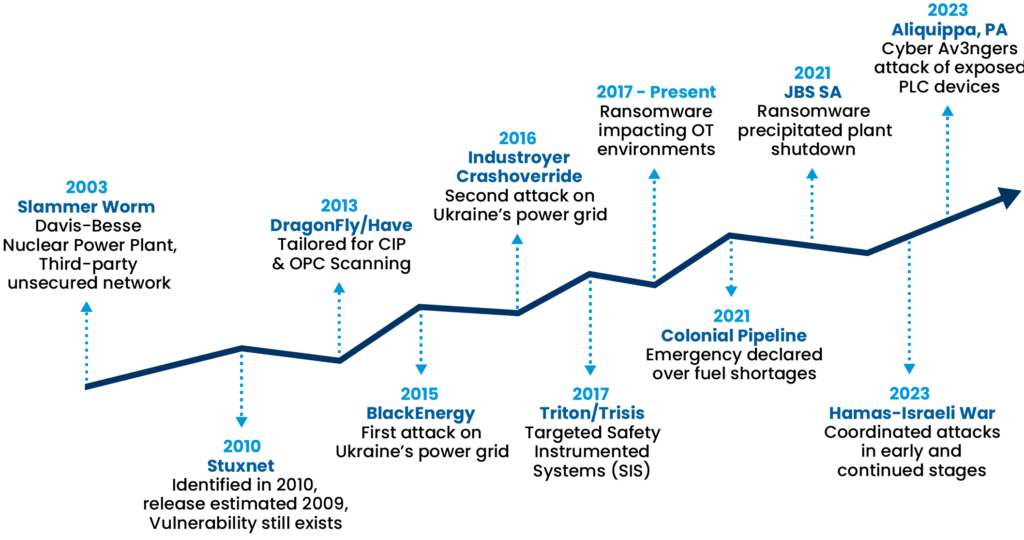
The increase in threat sophistication is evident in a variety of instances. Attackers have developed techniques that bypass traditional security measures, employing tactics such as zero-day exploits, advanced persistent threats (APTs), and sophisticated phishing campaigns. The July 2023 SANS Cybersecurity Threat Intelligence (CTI) report identified that phishing is chosen as the attack vector 98% of the time by threat actors, and that 36% of the time, these exploits are successful against their human targets.
These methods are designed to penetrate defenses without detection, allowing adversaries to establish a foothold within networks from which they can launch further attacks or conduct espionage. Starting with Stuxnet in the 2009-2010 timeframe, the increased sophistication in cyberattacking process control and automation systems makes identifying control system cyberattacks problematic, as the hackers are using techniques that make cyberattacks look like equipment malfunctions; not actual cyberattacks.
The nature of OT environments—almost always characterized by a mix of old and new technologies, with legacy systems operating alongside modern digital solutions—presents unique challenges. Originally designed for open architecture and communication, these environments do not inherently have cybersecurity, making them fundamentally more vulnerable to today’s advanced threats and even older threats. Attackers exploit these vulnerabilities, using knowledge of specific control systems and protocols to cause disruption, sabotage, or even physical damage marked by an escalation of targeted attacks. One such example is the Maroochyshire, Australia wastewater cyberattack in 2000 and China’s 2001 cyberattack on the California Independent System Operator (CA ISO oversees most of the state’s electrical grid).
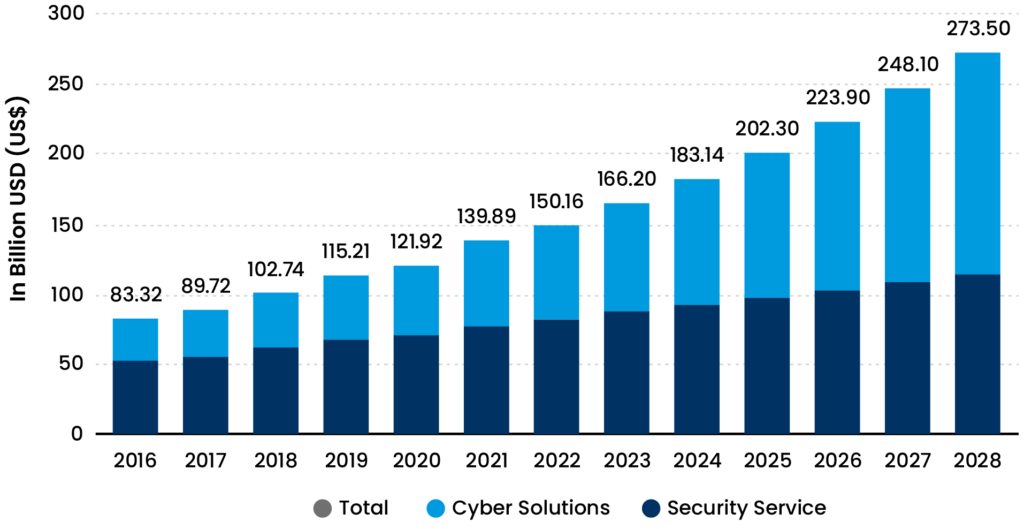
To combat the increase of sophisticated attacks, the global response was to increase spending on cybersecurity products, services, and solutions. In 2023 alone, market analysts conservatively report numbers somewhere between $167B USD and $191B USD. Most analysts also agree that these numbers will continue to rise, projecting 2028 numbers of $259B USD or higher.
This proportional surge in global spending on cybersecurity products and services, intriguingly, has not resulted in a corresponding increase in the effectiveness of risk mitigation. This paradoxical situation suggests a reality where the remedies proposed by the cybersecurity industry might, in fact, be exacerbating the problem, leading to a scenario where “the cure is worse than the disease.”
The landscape of cybersecurity products, services, and solutions, characterized by their complexity, are designed to offer comprehensive protection against an array of cyber threats (most of those being advanced threats) even though OT systems are still vulnerable to older, more unsophisticated threats. But this approach to inclusive protection does little to address the Cyber-Physical Systems security requirements, that have more to do with physics, and the need to think holistically and more practically when protecting OT environments, where the physical and digital worlds connect.
A recent example of this cyber-physical attack was demonstrated in Poland. Andy Greenberg wrote an article on August 27, 2023, in Wired, titled The Cheap Radio Hack That Disrupted Poland’s Railway System, “…the saboteurs appear to have sent simple ‘radio-stop’ commands via radio frequency to the trains they targeted. Because the trains use a radio system that lacks encryption or authentication for those commands…anyone with as little as $30 of off-the-shelf radio equipment can broadcast the command to a Polish train—sending a series of three acoustic tones at a 150.100-megahertz frequency—and trigger their emergency stop function.”
According to Joe Weiss, ISA Life Fellow, IEEE Senior Member, and Emeritus Managing Director of ISA99, “control systems were designed based on the KISS principle – ‘Keep it simple stupid’. Unfortunately, cybersecurity and operational performance are mutually exclusive, which makes cybersecurity implementations in an OT environment inherently complex.”
“Proactive OT cybersecurity involves strategic investments and measures to prevent incidents rather than just reacting to them.”
Joe Weiss – ControlGlobal – Unfettered (blog) – November 29, 2023
This complexity itself has become a double-edged sword. Configuration errors, integration challenges, and the daunting task of managing and updating many security tools have inadvertently increased vulnerabilities within OT environments.
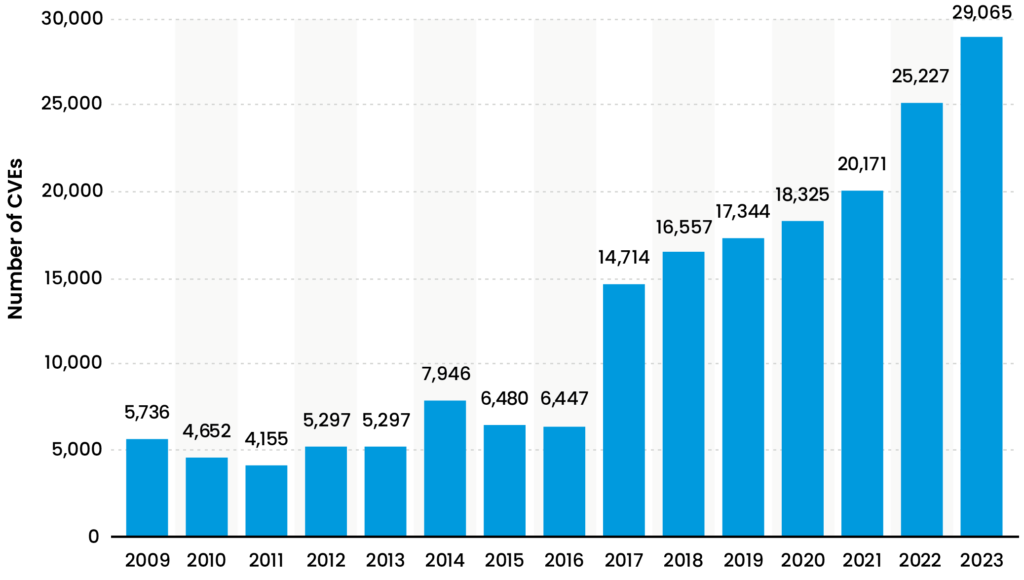
Cybersecurity complexity obscures rather than protects, creating gaps that attackers are all too ready to exploit; not to mention the tens of thousands of exploits and vulnerabilities that are identified in CVE tracking of the cybersecurity products and solutions industry, to the benefit of practitioners, as well as threat actors, as seen in the graphic below. Additionally, complexity can cause unintentional impacts and can stress an already overburdened work force that is generally not accustomed to dealing with the extra complexity.
The argument for simplicity in cybersecurity emerges as a compelling antidote to this challenge. Simplicity in security measures significantly enhances the manageability and effectiveness of threat mitigation strategies. By reducing the complexity of cybersecurity solutions, organizations can achieve better visibility and control over their OT environments, leading to more robust protection against cyber threats while minimizing the potential threat to reliable operations.
By reducing cybersecurity complexity, while combining the success of OT asset protection best practices, such as network segmentation, isolation, and flattening of networks, production operations realize not only uptime, productivity and (most importantly) safety, but also the cost-effective and appropriate security. Another very important benefit is the ability to use the existing workforce without having to bring in additional resources.
The marketing message from the cybersecurity industry for protecting OT networks and assets has been ‘More is More…buy more and you are more secure.’ More hardware, more software, more services, more, more, more. While this is good for the revenues of the multibillion-dollar security manufacturers, it is not good for control systems or OT environments. Certainly, some of the cybersecurity innovations are warranted, but not to the quantities propositioned by the manufacturers…whose perceived message is, “if 1 firewall is good, then 5 should be great, right?” Wrong.
Mr. Weiss went on to say, “actual cases demonstrate increased complexity from conventional cybersecurity tools in OT environments have increased not reduced operational risks. These include the FortiGate firewall vulnerabilities and the Ivanti VPN vulnerabilities. In another case, a disturbance caused by the implementation of a device locking security tool in response to NERC CIP compliance resulted in the loss of SCADA services. There needs to be a better way to add cybersecurity while minimizing complexity. Technologies to do this exist.”
Simplifying cybersecurity strategies involves a meticulous reassessment of risks, a consolidation of security tools and vendors, and a renewed focus on staff training and awareness. Such an approach not only enhances the security posture of OT environments, but also ensures that security measures are sustainable, manageable, and adaptable to the evolving threat landscape.
Mr. Weiss has been addressing this topic for over 25 years. His book, “Protecting Industrial Control Systems from Electronic Threats,” was one of the first published works to address the issue of using Bluetooth connections to access smart grids. His blog www.controlglobal.com/unfettered, addresses the consequences of improper or non-secured network access, and the challenges that OT leaders face.
First, those responsible for OT environments must understand the systems they’re responsible for protecting:
https://www.controlglobal.com/home/blog/11414863/information-technology.
Mr. Weiss also offers a startling snapshot of what hackers can do once they achieve intrusion:
Case Study: Successful OT Security Implementation
Schneider Electric (SE) delivered over $500,000 in operational savings to a national food & beverage distillery by helping them to implement a top zero trust breach prevention solution to protect critical command and control operations. With minimal integration requirements and minimal disruption, this global corporation brought a secure remote access solution to its customer’s OT security strategy.
CLICK HERE to read the full success story.
Final Thoughts
To effectively protect OT systems, several key takeaways should be kept in mind. First, implementing strong access controls and authentication mechanisms is essential to prevent unauthorized access. Second, regular monitoring and threat intelligence can help identify potential vulnerabilities and mitigate risks. Third, conducting regular audits and assessments can help identify gaps in security and ensure compliance with industry standards. Finally, fostering a culture of security awareness and training among employees is vital to enhance overall OT security. By implementing these measures, organizations can strengthen the security posture of their OT systems and safeguard critical operations. An additional benefit is the improved reliability of the OT networks and control systems.
Best practices for OT cyber-physical security for Safety, Productivity, and Reliability
- Asset Management: Identify All Critical Assets and Data
- Periodic Risk and Vulnerability Assessments for Assets
- Personnel Training Programs and Education
- Operations Monitoring and Incident Response
Embracing simplicity in cybersecurity represents a strategic pivot towards improved effectiveness and resilience. It is a recognition that, in the face of increasingly complex threats, the clarity and straightforwardness of our defense mechanisms can be our greatest strength. By advocating for a cybersecurity culture that values simplicity, organizations can safeguard their critical infrastructure more effectively, ensuring that they are prepared to meet the challenges of the digital age with confidence and agility.
The shift towards simplicity is not just a tactical adjustment but a strategic imperative for securing the future of operational technology environments.
SUBSCRIBE to our blog for more information on OT security in future posts.
CONNECT with us on LinkedIn


