MITRE has gone to great lengths to outline the nature and intensity of common cyber-attack approaches and techniques, which they have captured in their MITRE ATT&CK Matrix for Enterprise. We have examined this matrix to find those sweet spots where our LinkGuard™ solution intervenes to provide front line cyber defense. Let’s take a closer look at some of these areas and how our solution provides protection against them.
Initial Access: This is the first stage of an attack where an adversary gains access to a network or system.
- With LinkGuard, we employ advanced authentication methods such as multi-factor authentication to prevent unauthorized access.
Execution: This is when an adversary executes malicious code on a targeted system.
- Our solution is able to segment a network, and obfuscate assets to block unknown or suspicious code, making it difficult for attackers to find and exploit vulnerabilities.
Persistence: Once an attacker gains initial access, they try to maintain their foothold within a network through persistent methods such as backdoors and rootkits.
- LinkGuard constantly monitors for any unusual activity and can quickly shut down these persistent techniques.
Defense Evasion: Attackers are constantly finding ways to evade security measures put in place by organizations.
- With our CyberCloak capabilities, we make it even harder for them to identify and exploit critical assets and data.
Our powerful solution utilizes quantum resistant technology to protect critical assets and data with our signature CyberCloak™ capabilities. We specialize in operational technology security and are constantly evolving our techniques to stay ahead of cyber threats. These capabilities are:

One of the key principles we follow is the concept of zero trust. This means that we do not automatically trust any user or device within a network, and instead verify their identity and permissions before granting access to sensitive resources. This approach helps prevent lateral movement within a network, one of the tactics commonly used by cyber attackers. We understand the importance of securing operational technology (OT) in today’s digital landscape. Many critical infrastructure systems, such as power plants and transportation networks, rely on OT for their operations. Our team of experts has a deep understanding of industrial control systems (ICS) security and our solution is specifically designed to protect these systems from cyber threats.
In addition to providing protection against specific areas listed on the MITRE ATT&CK Matrix for Enterprise, our product also supports the zero trust model. This means that we do not trust any user or device by default and constantly verify and authenticate their access to resources. Our focus on Zero Trust, in alignment the the U.S. Department of Defense requirements, is shown below.
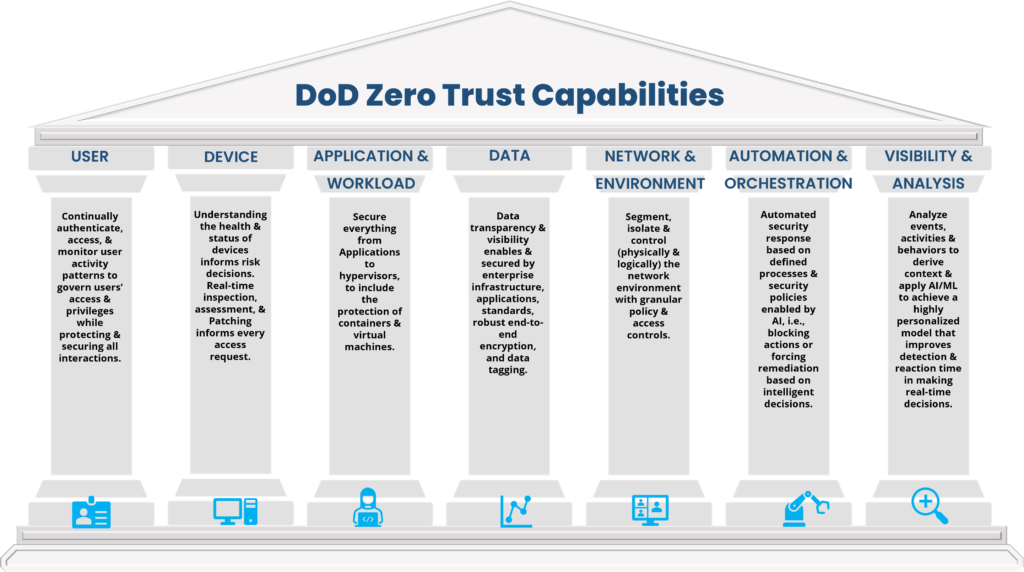
According to the U.S. Department of Defense, “Zero Trust is the modern strategy for cybersecurity. It assumes no implicit trust and requires verification of all who request access to our systems and networks. This approach fundamentally shifts our cybersecurity paradigm from one of mitigating risk after a breach to one of preventing such breaches in the first place.” LinkGuard’s CyberCloak capabilities are designed for precisely that – – “…preventing such breaches in the first place.”
Fortified with quantum resistance, LinkGuard offers network protection against a wide range of threats, making it an essential tool for any organization’s cybersecurity arsenal.
In conclusion, the rise of digital transformation has amplified the need for robust security measures in the operational technology space. LinkGuard, fortified by quantum resistance and the principles of a zero-trust model, emerges as a solution designed to deter and prevent potential breaches. Crucially, it addresses, head-on, four major cyberattack scenarios identified in the MITRE ATT&CK Matrix for Enterprise. This capability makes LinkGuard an instrumental asset for organizations, enhancing their cybersecurity landscape by mitigating risks and safeguarding critical infrastructure from evolving cyber threats.





