Introduction
As we stand on the precipice of the quantum future, the necessity to start driving NOW toward achieving quantum resilience cannot be overstated.
Resilience Today = Security Tomorrow
According to the resource Inside Quantum Technology News, the rapid developments in quantum computing are making current cybersecurity protocols increasingly vulnerable. Existing encryption methods are likely to be easily broken by powerful quantum computers, posing severe threats to data security. The advent of quantum computers has initiated a race against time as entities scramble to develop and implement quantum-resistant algorithms. Therefore, it is critical for organizations to update their cybersecurity strategies NOW to become quantum-resilient and maintain the security and integrity of their data in the quantum future.
Understanding Quantum Computing and Its Impacts
In our last blog post entitled “Introducing Quantum Computing And Its Implications” we defined Quantum computing, and described its general impacts. Quantum computing is rooted in the principles of quantum mechanics. It enables the processing of massive amounts of data at unprecedented speeds; yet, its potential impacts extend far beyond expedited computing – it threatens to dismantle the very fabric of our current cybersecurity infrastructure.
Quantum cryptography, sometimes referred to as quantum encryption, leverages the principles of quantum mechanics to secure communication and safeguard information. It uses individual particles of light (photons) to physically transfer a key between two parties. Owing to the peculiar properties of quantum mechanics, if an outsider attempts to observe the key in transit, it will alter the key in a way that is observable to the recipient, thus providing an inherent level of security.
Today, advancements in quantum cryptography are revolutionizing the way we approach cybersecurity. For instance, IBM’s research team has made significant strides in the development of quantum cryptography algorithms. As highlighted in IBM’s blog, they’ve been working meticulously on a lattice-based cryptography – a promising candidate for post-quantum cryptography. This innovative approach is designed to protect sensitive data even against future quantum computers, thereby spearheading efforts towards a quantum-protected future.
Quantum Threats to Cybersecurity
Quantum computing, if wielded maliciously, exposes grave vulnerabilities in our cybersecurity systems. Today, the landscape involves the stance of data collection now / decrypt later. Quantum computers can decrypt most encryption algorithms currently safeguarding our sensitive information, effectively rendering them obsolete. Cases such as the decryption of RSA-2048 in a hypothetical quantum future underscore the magnitude of these threats.
One practical example of how quantum computing can break current encryption is its potential to quickly solve the prime factorization problem, which is the foundation of RSA encryption. In RSA encryption, the security of data relies heavily on the computational difficulty of factoring large prime numbers. A large-scale quantum computer, using Shor’s algorithm, could theoretically perform this task exponentially faster than classical computers, thereby breaking RSA encryption.
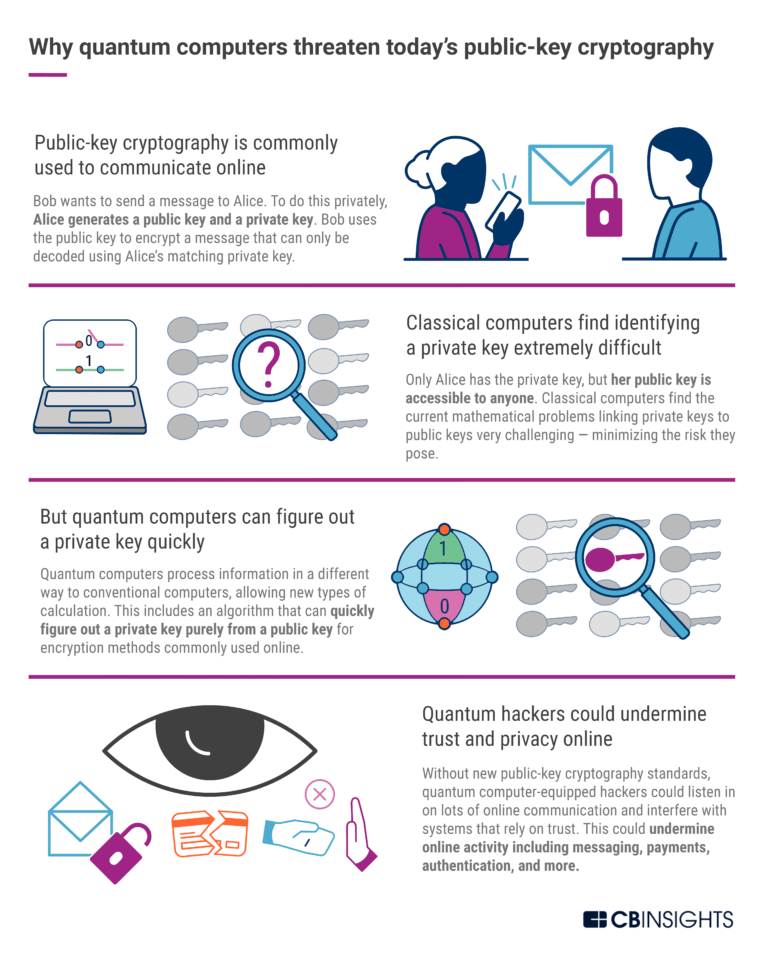
Fig 1. A graphic example by CBInsights illustrating how quantum computers can threaten public-key cryptography.
This potential vulnerability underscores the urgency and importance of developing advanced cybersecurity measures, such as quantum cryptography, that can withstand potential quantum threats.
What is Quantum-Resilient Cybersecurity?
Combatting quantum computing cybersecurity risks necessitates a comprehensive overhaul of our security systems. Quantum-resistant algorithms are the cornerstone of quantum resilient security, alongside a culture of continuous learning and adaptation. CTOs, CISOs, and CIOs must spearhead this charge, ensuring their teams are prepared for the quantum shift.
Any entity, governmental, public, or private that fails to become quantum resilient faces potentially catastrophic risks, as outlined in The Quantum Computing Report by the Global Quantum Institute (GQI). The report emphasizes that in the advent of quantum computing, traditional cybersecurity measures will fall short. Quantum computers have the capacity to decrypt standard encryption protocols, laying bare sensitive data and intellectual property, and risking immense financial and reputational damage. The report also warns of ‘harvest and decrypt’ attacks, where malicious entities could steal encrypted data today, to decrypt it when quantum computing becomes widely accessible. Simply put, failure to adopt quantum-resilient measures could jeopardize a company’s entire digital infrastructure, rendering it defenseless in the face of quantum-powered cyber threats.
Steps Toward Achieving Quantum Resilience
The time is now to build quantum-resilient cybersecurity solutions. It’s crucial to remain vigilant and proactive as quantum advancements continue to advance. Staying abreast of these developments is not merely an option; it’s an existential necessity.
The CISA, NSA, and NIST Factsheet on Quantum Readiness emphasizes a number of crucial points:
- Understanding Quantum Risks: The report highlights the importance of understanding and preparing for the potential risks that quantum computing presents to current encryption methods.
- Readiness to Transition: Organizations should be prepared for a smooth transition from classical algorithms to quantum-resistant algorithms. The transition should be viewed as an upgrade rather than a wholesale replacement.
- Preparation Time: It could take a decade or more to prepare for the advent of quantum computing. Therefore, starting the transition to quantum resilience now is crucial.
- Use of NIST’s cryptographic standards: The factsheet encourages the use of NIST’s cryptographic standards as they are developed to ensure that organizations are implementing the most effective and current quantum-resistant algorithms.
- Collaboration is Key: The document underlines the importance of national and international collaboration in research and development, standardization, and knowledge sharing in the field of quantum computing and quantum cybersecurity.
As your organization works to secure quantum resilience, it’s important to tic through this checklist of actions:
- Initiate Quantum Awareness Training: Organizations must invest in training programs to increase understanding of quantum risks and the importance of quantum resilience among employees at all levels. This is the first step in promoting a culture of quantum readiness.
- Engage Quantum Security Experts: Engaging specialists with expertise in quantum computing and quantum-resistant algorithms is essential for the development and implementation of quantum-resilient security measures.
- Invest in Quantum-Resilient Technologies: Invest in and adopt quantum-resistant encryption algorithms and other technologies that are designed to withstand quantum computing threats.
- Establish a Quantum Resilience Team: Form a dedicated team responsible for keeping up with the latest in quantum computing and quantum cybersecurity, and developing strategies to mitigate potential risks.
- Regularly Review and Update Security Measures: Quantum technology is rapidly evolving. Regular review and updates of security measures are necessary to ensure they remain effective against the latest quantum threats.
Conclusion
The call to action is clear: we must begin working towards quantum resilience today. Breaking Defense strongly echoes this perspective through their article entitled “All systems need to be hardened: Officials, industry sound the alarm on quantum threat to encryption.” “You don’t need a quantum computer to start laying the foundations for a quantum-powered hack — or, fortunately, to start building a defense.” A recent McKinsey report states, “…full security when information is transferred between locations. Quantum-encryption protocols are more secure than classical protocols, most of which will likely be able to be broken once quantum computers attain more computing power or can work with more efficient algorithms.” As we grapple with the implications of quantum computing, let us remain steadfast in our commitment to securing our digital landscapes. After all, the quantum future waits for no one.
To learn more about our CyberCloak quantum resistance capabilities, visit: https://blueridgenetworks.com/linkguard/





